Fixing The React2Shell Vulnerability in Large and Complex Enterprise Codebases (Part 2)
This post builds on our previous post (hereafter Part 1) on using Sourcegraph to address CVE-2025-55182. The purpose of this post is to describe how you can automate this remediation process and track organizational progress across your codebase. We focus on four capabilities required to complete remediation at scale: Batch Changes, Sourcegraph MCP, and Deep Search.
Part 1 showed how to identify every repository containing vulnerable versions of:
react-server-dom-webpackreact-server-dom-parcelreact-server-dom-turbopack
For example, you can use the simple query:
context:global file:package.json "react-server-dom-(webpack|parcel|turbopack)":\s*"[~^]?(19\.0(\.0)?|19\.1\.[01]|19\.2\.0)" patterntype:regexp
to rapidly find potentially vulnerable repositories (when searching thousands of repositories across a variety of code hosts this search takes ~8 ms). Finding these instances is only the first step. Large engineering organizations do not manually fix these vulnerabilities. Dependency changes must be applied consistently across all impacted repositories, lockfiles must be regenerated, branches must be created, and pull requests must be opened. Doing this manually is slow and error-prone, making it challenging to repeat reliably.
This is where Batch Changes enters the workflow.
Automate upgrade patches across all affected repositories
Once you’ve identified the affected repositories or the query that matches them, the next step is to apply consistent, safe upgrades to these repositories. Manually updating hundreds of codebases is not practical; Batch Changes enables an automated process that finds affected repositories, creates patches, commits them, and opens pull requests across all your repositories in parallel. Using the query from Part 1, you can use the repositoriesMatchingQuery field to apply your changes to each of the vulnerable repositories.
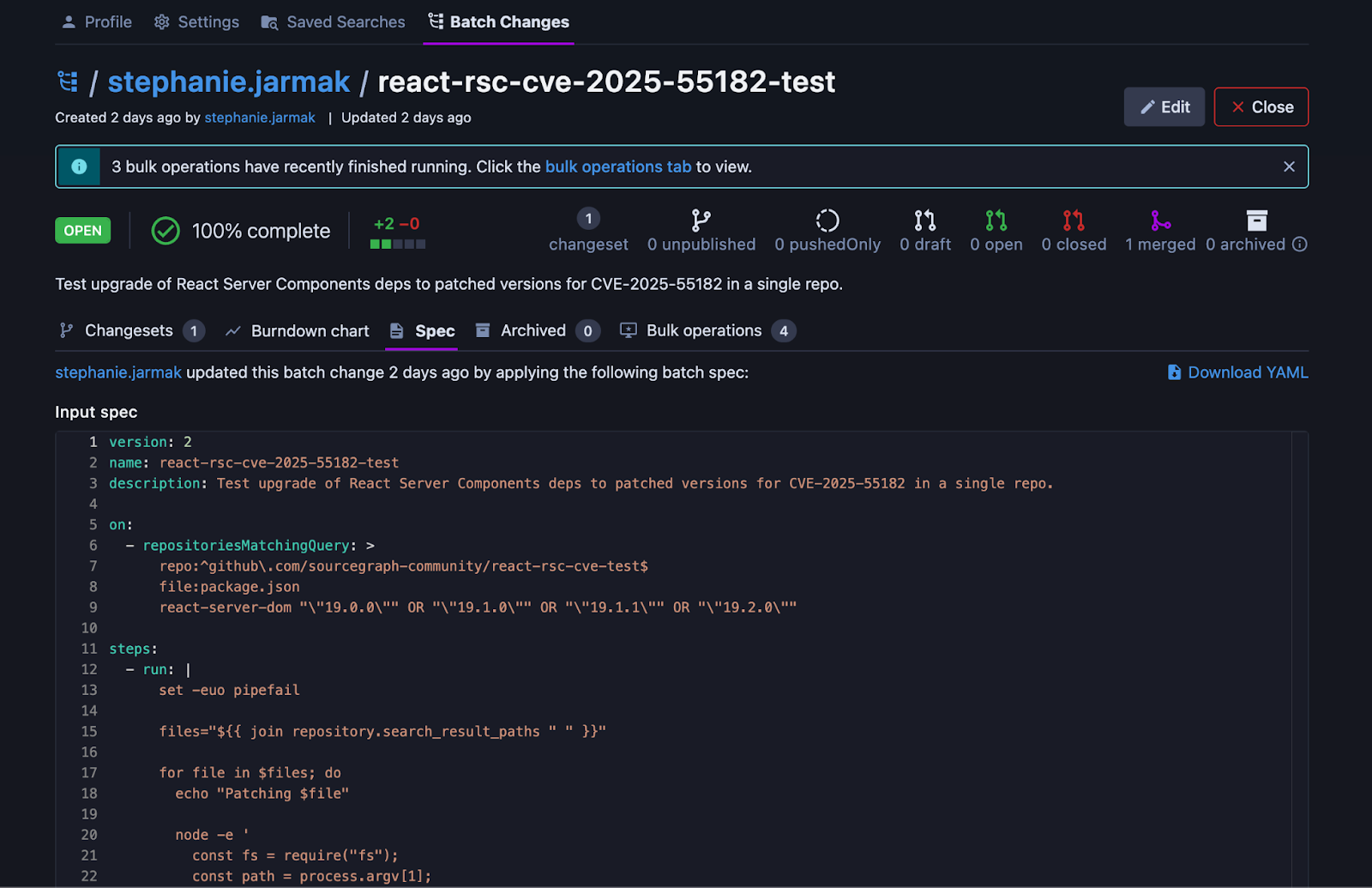
View of the Batch Changes spec for our specific example.
- Detects vulnerable versions (
19.0.0, 19.1.0, 19.1.1, 19.2.0) - Upgrades to patched version
^19.2.1 - Regenerates lockfiles
- Creates a branch + commit
- Opens a pull request
This defines the upgrade once and applies it everywhere.
If your organization also uses Next.js, then you would follow a similar process to identify vulnerable repos and use Batch Changes to apply fixes (15.x patched builds, 16.0.7, 14 replacing 14.3.0-canary). Here are generalized Batch Changes scripts you can use to address these React and Next.js vulnerabilities using the queries from Part 1 to identify vulnerable repos instead of specifying a known vulnerable repo.
Using the Sourcegraph MCP server to find and fix vulnerabilities
If you prefer to completely automate this process end-to-end, then we recommend using our MCP server, where you can use any agent to:
- Find all repositories containing a vulnerable version
- Find all files containing vulnerable lines
- Generate batch changes YAML script
- Use the Sourcegraph CLI to execute batch changes
Example MCP query that finds repositories containing vulnerable React Server Components:
find repos with vulnerable versions of React 19.0, 19.1.0, 19.1.1, 19.2.0
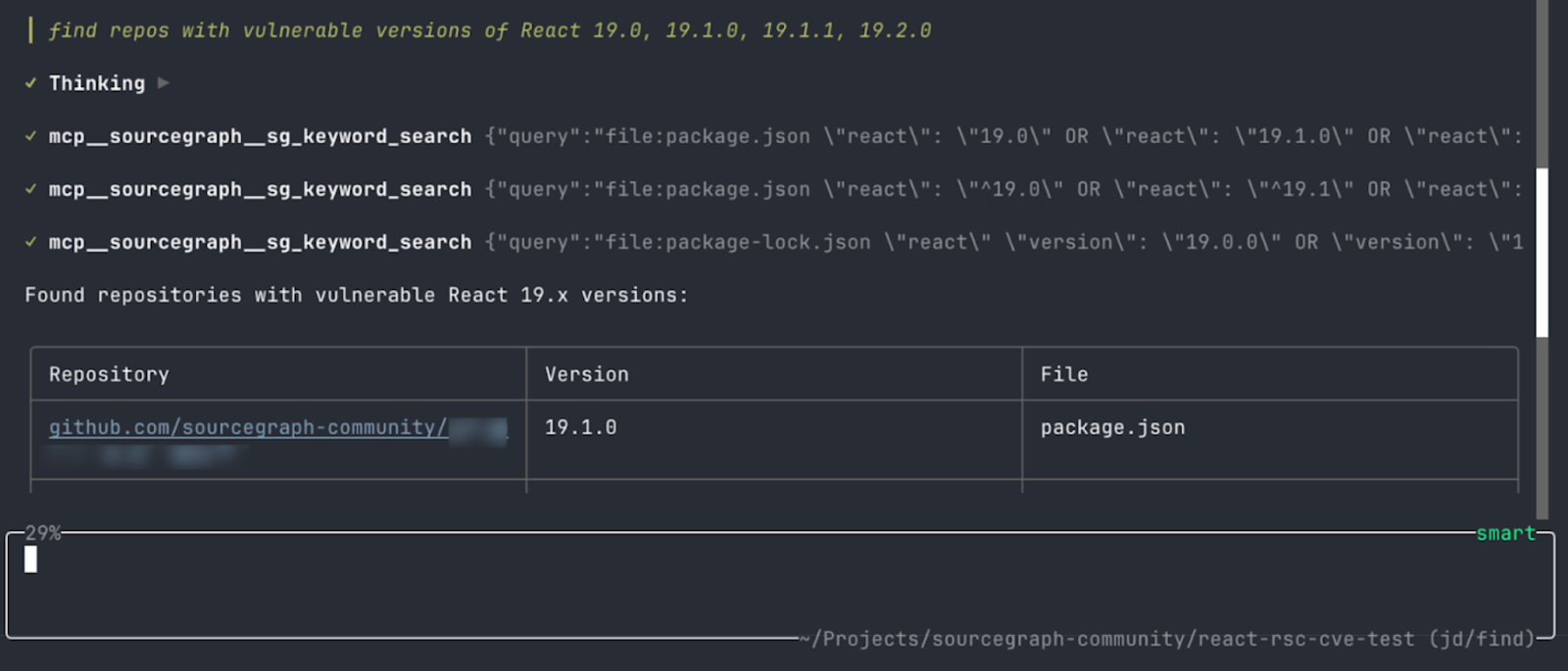
You can then pass the Batch Change documentation or start from a template in the Batch Changes UI to draft your Batch Changes script.
Automate PRs to fix the React Server Components vulnerability across all your code
After you (or your agent) create the batch script, you (or your agent) can then use the Sourcegraph CLI to execute it, or you can create and run the batch change directly through the UI.
Example using the Sourcegraph CLI:
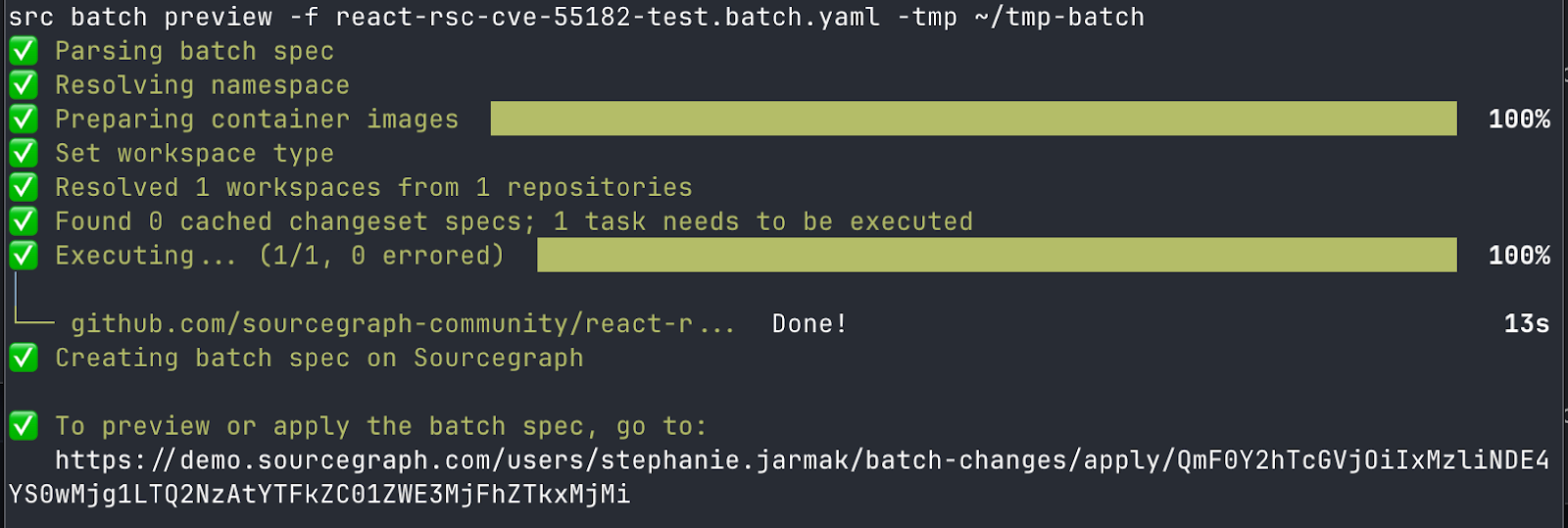
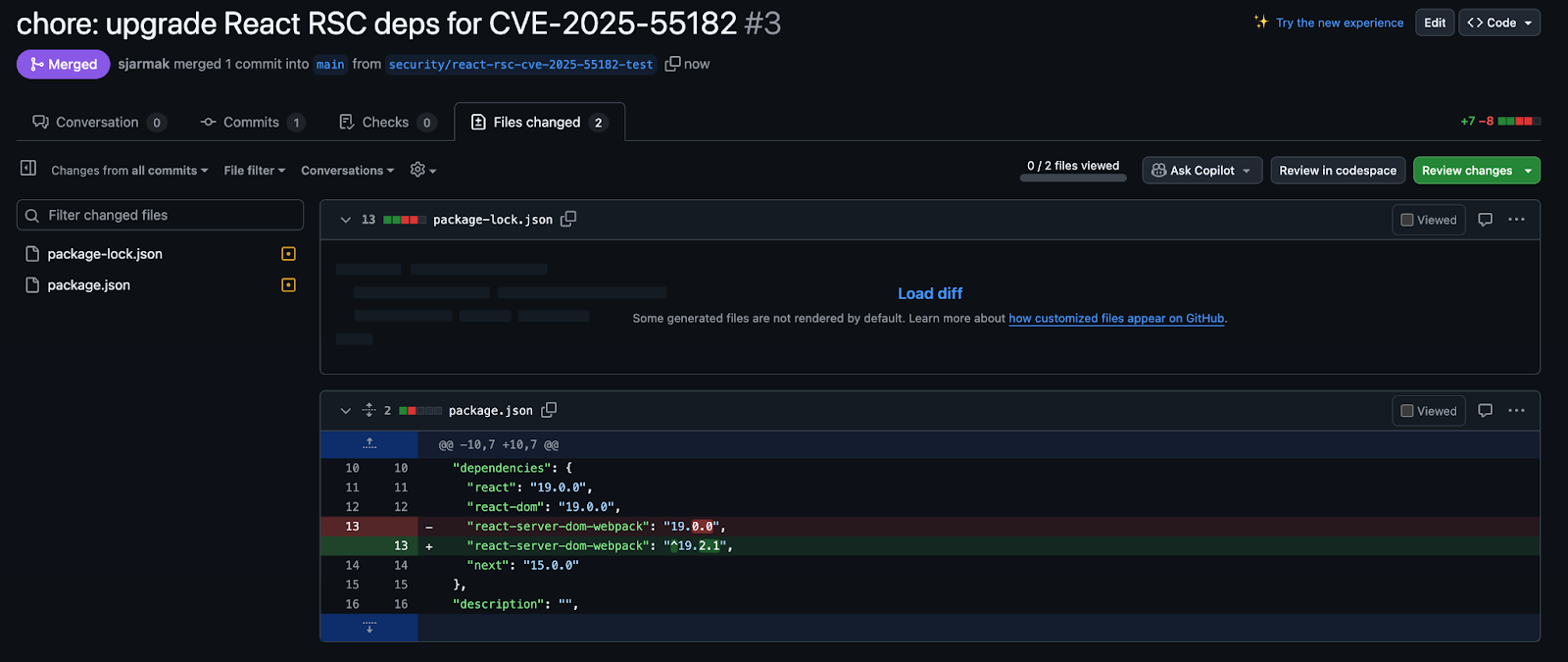
After executing the Batch Change, you have the opportunity to preview the modifications before they are published as a pull request across the affected repositories. Once you look over the preview in the UI (see example below), you can then publish the changes.
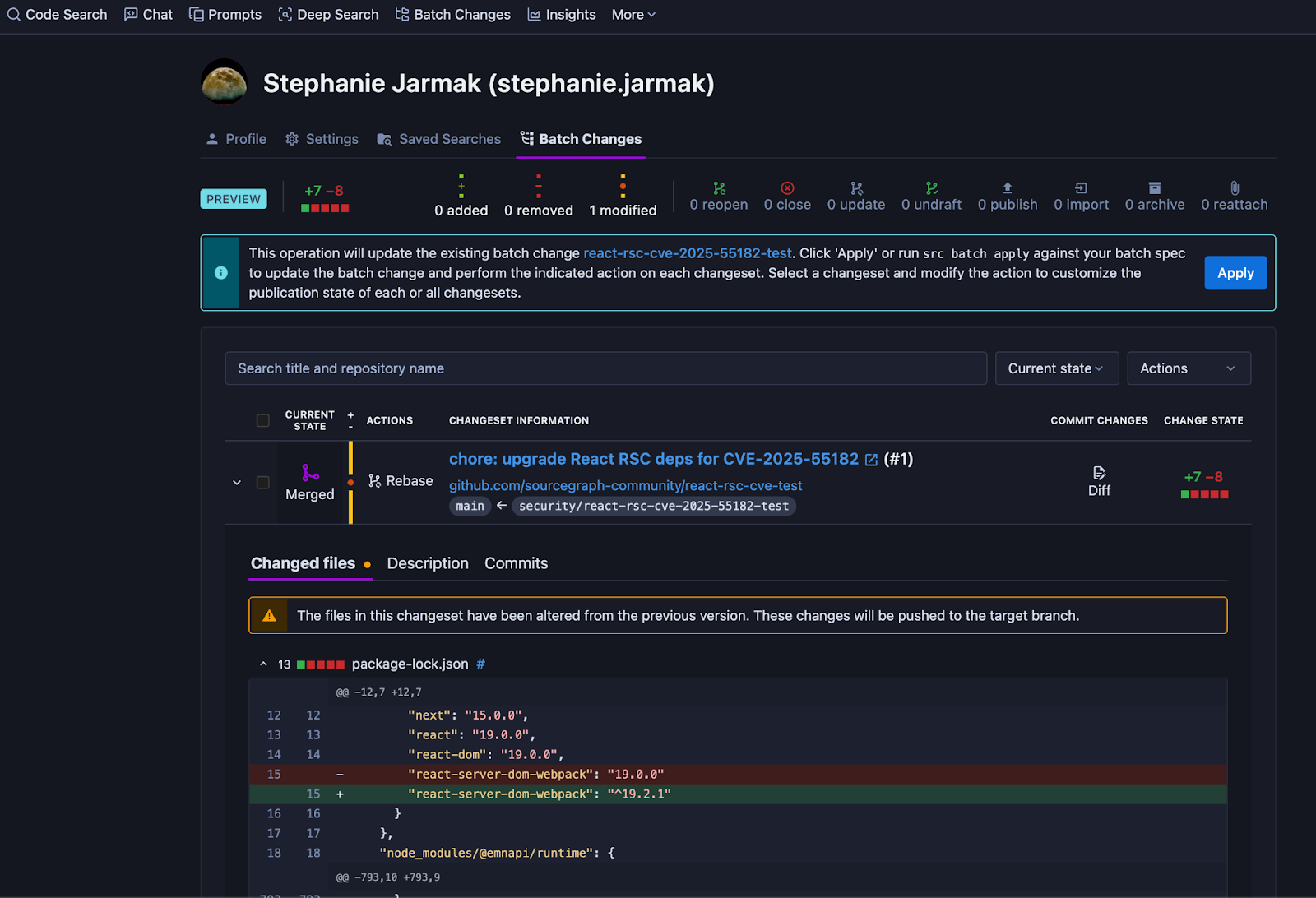
Then you can publish the change as a PR in GitHub where it can be merged.
Track the progress of applying fixes across all your code
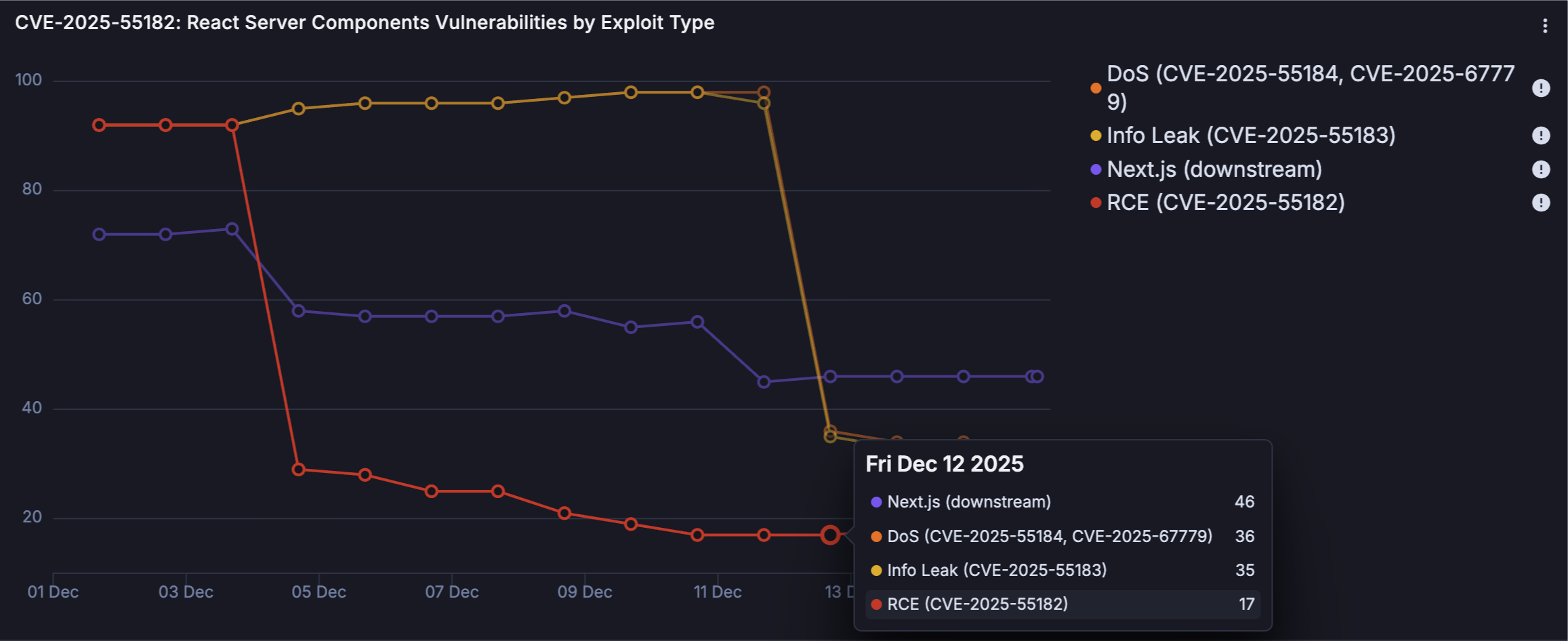
To track vulnerable vs. fixed files across your repositories over time, you can add a data series that corresponds to matches with vulnerable versions and a data series that finds matches of the fixed versions.
Here is an example where we are tracking the migration from the PR in our test repository created from our Batch Changes script. We selected the repository explicitly here, but you can also assign repositories that match a particular query (e.g., the query we used earlier to identify the list of repos in our instance that are affected by the vulnerability).
Using Deep Search to validate full remediation
Deep Search enables semantic follow-ups:
- “Are any repositories still importing vulnerable versions of RSC?”
- “Are any lockfiles still referencing 19.1.1?”
- “Do any build artifacts still package vulnerable versions?”
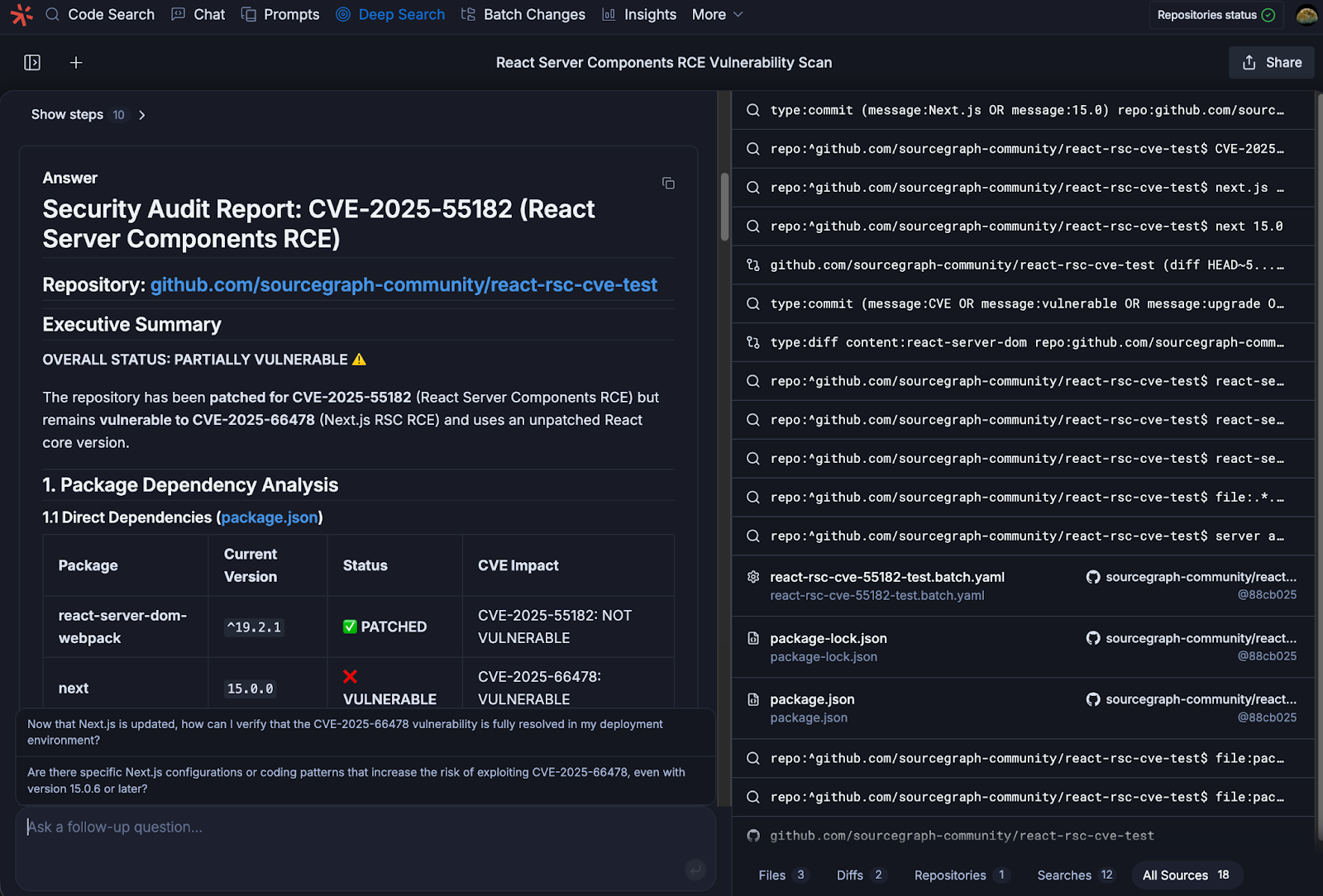
Deep Search’s agentic search process enables you to easily check for any remaining vulnerabilities by translating natural-language into complex Code Search queries that identify all instances across your system. You can see in our example we fixed one vulnerability but neglected to include patches for other impacted versions, and Deep Search has alerted us that we should make these changes.
End-to-end workflow summary
- Identify vulnerable React Server Component versions (Part 1)
- Automate vulnerability fixes using the Sourcegraph MCP
- Apply upgrades at scale with a single Batch Changes spec
- Verify full remediation using Deep Search
Sourcegraph helps you complete the code security lifecycle from detection → remediation → verification.
Getting started with Sourcegraph
Schedule a conversation to see how Sourcegraph can help you and your team find code, make large-scale changes, and track changes across codebases of any scale and with any number of code hosts.
.avif)

